- Pro
- Security
MuddyWater uses a fake Snake game to gain persistence
Comments (0) ()When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
 (Image credit: Shutterstock)
(Image credit: Shutterstock)
- An Iranian-aligned group is targeting Israeli and Egyptian infrastructure
- The group's previous attacks have been noisy and easy to detect
- New techniques and malware have been deployed
An Iranian-aligned hacking group tracked as 'MuddyWater' has dramatically shifted tactics in attacks against Israeli and Egyptian critical infrastructure.
Previous campaigns by the group, observed by ESET Research, were characteristically noisy in their tactics, techniques, and procedures (TTPs) making them easily detectable.
However, the group has begun employing a new backdoor deployed via the Fooder loader, which often disguises itself as the classic Snake game.
You may like-
 Pro-Russian hackers tricked into attacking decoy target
Pro-Russian hackers tricked into attacking decoy target
-
 Russian speaking hacking group now shifting focus to government targets
Russian speaking hacking group now shifting focus to government targets
-
 Chinese hackers hit government systems, stealing emails and more - here's what we know
Chinese hackers hit government systems, stealing emails and more - here's what we know
MuddyVipers, snakes, and ladders
The attacks have typically targeted Israeli telecommunications, governmental, and oil and energy sectors. In this campaign, MuddyWater began by distributing spearphishing emails with PDF attachments linking to free remote monitoring and management (RMM) software, with the install files hosted on OneHub, Egnyte, Mega, and other free file hosting services.
Rather than installing legitimate RMM software, the files instead install loaders through which attackers can deploy backdoors. In the attacks observed by ESET, a newly identified loader known as Fooder deploys the MuddyViper backdoor.
Fooder has a unique characteristic - it often masquerades as the Snake game. This technique is more than just a disguise, as the core logic of Snake provides the loader with a custom delay function, allowing it to hide its true function from analysis.
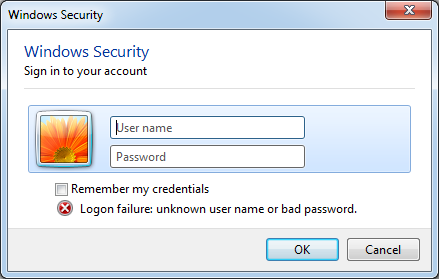
The MuddyViper backdoor is also previously unobserved. Written in the C/C++ programming language, MuddyViper is capable of collecting system information, downloading and uploading files, executing files and shell commands, and stealing Windows credentials and browser data by displaying a fake Windows Security dialog.
Are you a pro? Subscribe to our newsletterContact me with news and offers from other Future brandsReceive email from us on behalf of our trusted partners or sponsorsBy submitting your information you agree to the Terms & Conditions and Privacy Policy and are aged 16 or over.
The MuddyWater campaign targeted 17 organizations in Israel across a range of sectors including engineering, local government, manufacturing, technology, transportation, utilities, and universities. The group also targeted an Egyptian organization in the tech sector.
For greater insight into the MuddyWater campaign, as well as indicators of compromise, take a look at ESET’s 'MuddyWater: Snakes by the riverbank' research.
 The best antivirus for all budgetsOur top picks, based on real-world testing and comparisons
The best antivirus for all budgetsOur top picks, based on real-world testing and comparisons➡️ Read our full guide to the best antivirus1. Best overall:Bitdefender Total Security2. Best for families:Norton 360 with LifeLock3. Best for mobile:McAfee Mobile Security
 Benedict CollinsSocial Links NavigationSenior Writer, Security
Benedict CollinsSocial Links NavigationSenior Writer, SecurityBenedict has been with TechRadar Pro for over two years, and has specialized in writing about cybersecurity, threat intelligence, and B2B security solutions. His coverage explores the critical areas of national security, including state-sponsored threat actors, APT groups, critical infrastructure, and social engineering.
Benedict holds an MA (Distinction) in Security, Intelligence, and Diplomacy from the Centre for Security and Intelligence Studies at the University of Buckingham, providing him with a strong academic foundation for his reporting on geopolitics, threat intelligence, and cyber-warfare.
Prior to his postgraduate studies, Benedict earned a BA in Politics with Journalism, providing him with the skills to translate complex political and security issues into comprehensible copy.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
Logout Read more Pro-Russian hackers tricked into attacking decoy target
Pro-Russian hackers tricked into attacking decoy target
 Russian speaking hacking group now shifting focus to government targets
Russian speaking hacking group now shifting focus to government targets
 Chinese hackers hit government systems, stealing emails and more - here's what we know
Chinese hackers hit government systems, stealing emails and more - here's what we know
 Russian hackers hit Windows machines via Linux VMs with new custom malware
Russian hackers hit Windows machines via Linux VMs with new custom malware
 JSON services hijacked by North Korean hackers to send out malware
JSON services hijacked by North Korean hackers to send out malware
 A terrifying, self-replicating malwaere has infected npm packages with over 2 million downloads per week - here's how to stay safe
Latest in Security
A terrifying, self-replicating malwaere has infected npm packages with over 2 million downloads per week - here's how to stay safe
Latest in Security
 New data centers will need almost triple the current energy demand by 2035
New data centers will need almost triple the current energy demand by 2035
 Russian speaking hacking group now shifting focus to government targets
Russian speaking hacking group now shifting focus to government targets
 Glassworm returns once again with a third round of VS code attacks
Glassworm returns once again with a third round of VS code attacks
 107 Android flaws just got patched by Google - here's how to make sure you're up to date
107 Android flaws just got patched by Google - here's how to make sure you're up to date
 Huge cryptomixer takedown sees feds seize over $30milion
Huge cryptomixer takedown sees feds seize over $30milion
 4.3 million have installed this malicious browser extension on Chrome and Edge - here's how to check
Latest in News
4.3 million have installed this malicious browser extension on Chrome and Edge - here's how to check
Latest in News
 Grab a free Fortnite skin with your Backbone Pro
Grab a free Fortnite skin with your Backbone Pro
 Character.ai launches Stories as it scales back chat for under-18s
Character.ai launches Stories as it scales back chat for under-18s
 New Windows 11 'PC you can talk to' ad pushing Copilot is proving divisive
New Windows 11 'PC you can talk to' ad pushing Copilot is proving divisive
 Garmin attempts to drive more Connect+ signups by paywalling its Spotify Wrapped-style Garmin Connect Rundown
Garmin attempts to drive more Connect+ signups by paywalling its Spotify Wrapped-style Garmin Connect Rundown
 TCL’s new Samsung The Frame rival looks like a better TV, but is still missing the two most important features of The Frame
TCL’s new Samsung The Frame rival looks like a better TV, but is still missing the two most important features of The Frame
 Spotify Wrapped 2025 not showing up? Try these 3 fixes
LATEST ARTICLES
Spotify Wrapped 2025 not showing up? Try these 3 fixes
LATEST ARTICLES- 1Iranian hacker group deploys malicious Snake game to target Egyptian and Israeli critical infrastructure
- 2Grab a free Fortnite skin with your Backbone Pro
- 3Character.ai launches Stories as it scales back chat for under-18s
- 4Nvidia admits the $100bn 'biggest AI infrastructure project in history' OpenAI deal still isn't finalized
- 5New Windows 11 'PC you can talk to' ad pushing Copilot is proving divisive